What is risk mapping?
First and foremost, risk mapping consists of a table organised around a colour classification (“heatmap”) of threats to a company. Though its implementation seems simple, the organisation it entails is cumbersome and involves stakeholders at every level of a business.
Definition of risk mapping and schematisation
The French media company Agefi (an economic and financial agency) defines risk mapping as “identifying, evaluating, prioritising, and managing the risks which come with an organisation’s activities”.
As part of a risk management process related to cybersecurity breaches, risk mapping has two goals:
- identifying and managing key risks to ensure the organisation's cybersecurity;
- granting general management and the information systems division sufficient resources to set up successful and effective preventive measures.
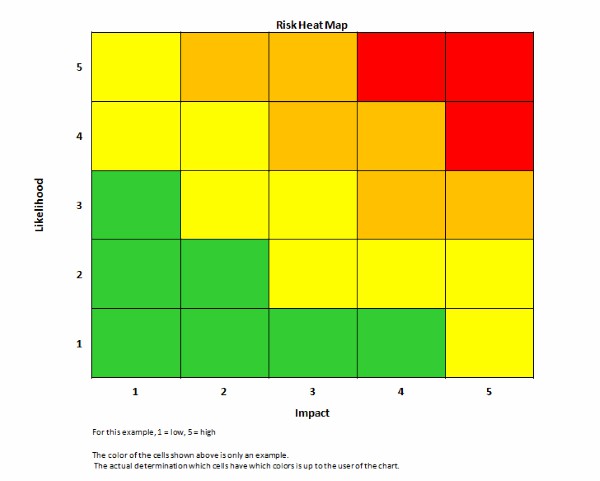
The result of this methodology is a map – a sort of graphic representation. It summarises a company’s risks within a double entry table:
- the horizontal axis represents a risk’s degree of seriousness, ranging from minor to major, or even “catastrophic” depending on the scale that you wish to adopt.
- the vertical axis illustrates the risk’s degree of probability, ranging from improbable to very probable/certain.
Companies sometimes reverse these axes when mapping, the probability then being on the x-axis and the severity on the y-axis. In all cases, the criticality of the risk corresponds to the ratio between its impact and its likelihood. So, risks mapped at the bottom left of the table represent a low probability and danger. The closer a risk is to the upper right of the table, the more tangible and serious the threat.
Colour codes often play an important role in risk mapping; the graph goes from green to red. Green is an acceptable risk and red is a critical risk, which may prove to be more than what your company can endure.
Who should be involved in risk mapping?
Ideally, the design of cyber risk mapping should include heads of all the business’ main departments. Each employee – from the managing director to the receptionist – is exposed to or actively involved in risk scenarios which must be clearly identified in order to be assessed: it is essential to include as many different departments as possible, from all levels of the organisation, from management down to operational staff.
From a cyber risk assessment perspective, the Chief Information Security Officer (CISO) naturally plays a major role in setting up the cyber risk map. Nonetheless, they need to cooperate with risk management and internal control, if your company happens to have such departments. Risk assessment cannot possibly be effective without flawless communication between divisions.
Why do you need to map risks?
As mentioned before, risk mapping is above all a risk management tool intended for the company's decision makers. It focuses on listing all the main risks a company faces, covering management, sales, human resources, cyber risks, corruption, and even natural disaster or health risks. The schematic visualisation of probabilities and impacts makes it easier to understand the risks to which your company is exposed.
Risk mapping can also be performed for each department of your organisation. In this case, the company carries out its risk assessment by category of hazard: one for cybersecurity, one for management, and another for human resources, etc. In the cybersecurity field, the risk table is intended to ensure everyone in every part of the organisation has a good grasp of IT-related risks, meaning that every department head is in an informed position to make the right decisions about cybersecurity.
Risk mapping is not a mandatory procedure. It can nevertheless be used as a proof that your company endeavours to uphold cybersecurity, in the context of a court of law. Besides, stock-listed companies have a duty to adopt an effective risk management strategy, by listing the major risks to which they are exposed.

Transform how you model, measure, and manage cyber risk.
Don't wait for the inevitable cyber incident. Build a resilient, risk-based cybersecurity program with CRQ.
How to successfully risk map your company
Once the general principle of risk mapping has been assimilated, you need to follow a few tips and guidelines so that this tool reaches maximum efficiency:
- Exhaustiveness also implies scalability: the map must be regularly updated and adapted to potential new threats;
- Naming the risks is not enough: you need to place them in the context of overall company operations;
- The way in which the frequency and severity of hazards is determined should be defined and described in the appendix to the risk table, as specified by ISO 27005. For a substantial projective value, you might want to pair risk mapping with a quantitative method of financial risk assessment. An approach such as VaR (Value at Risk) consists of collecting statistical data in order to establish probability estimates of cyber risks. It is far more thorough and reliable than qualitative approaches.
- This mapping document must be easy to understand and remain accessible to all employees.
Keeping this objective of legibility in mind, some structures choose to rank their key risks by number. This is notably McKinsey & Company’s risk measurement strategy. The consulting firm suggests associating cyber risk mapping with a note from 1 to 4 for the main cyber risks. In the example below, four key risks are featured: disruption of online services (1), data breach (2), cyber fraud (3), risk related to suppliers or vendors (4).

You can use this numbering strategy to increase understanding among employees who do not take part in the development of your risk mapping. This type of risk matrix is dependent on your task force’s subjectivity, so you should talk the rest of your employees through the details. Indeed, as documented in ISO270005 section 8.3 and Addendum E2, this qualitative approach, based on nominal or ordinal scales, is heavily biased. It leaves little room for reliably comparing scenarios or protective measure efficiency, and it does not really help the decision-making process. The issue here is not the graphic representation, but rather the probability and impact measurement methodology, which is unreliable.
What methods can be used in cyber risk mapping?
A proper risk mapping procedure comprises at least four stages. This approach is the most conventional one, it aims to identify the company's core operation and the associated risks.
The standard risk mapping approach in 4 stages
In many cases, risk mapping simply includes four stages:
1 / List the main activities of your structure and its key assets;
2 / Identify the threats with which it could be confronted. This phase is about determining the vulnerabilities of your company. Here, list the problematic situations that could put your company in a crisis situation or even threaten its survival. When it comes to cybersecurity, you have to consider every potential cyberattack: DDoS attack, phishing, ransomware, man-in-the-middle attack (MITM), and other malware.
3 / Evaluate the impact and the likelihood of those risks. A cyberattack can impact the reputation of the company, cause disruption to its operations, effect its financial assets, or compromise the personal data of users and customers.
Allocate a degree of severity to each of these consequences: green, yellow, orange, or red. Then assign each of those risks a probability of occurrence, again green (unlikely) or red (very likely). By using this classification, you should have a risk map organised around four levels of abscissa and four levels of ordinates.
Note that this risk ranking method – both nominal and ordinal – conveys personal and subjective evaluations, which are influenced by the representations of your task force members as well as their own personal experiences. For optimal prevention, you could perhaps consider complementing your risk mapping with the main cyber risks’ financial quantification methods. Thanks to scientific studies, it has been shown that even experts often are victims of a high degree of subjectivity (see Harvard Business Review and 19710101 - Amos Tversky and Daniel Kahneman - belief-in-the-law-of-small-numbers-stats-org-uk.pdf).
4 / Determine what measures you should take to detect cyber risks before a crisis occurs, then evaluate the means which could help mitigate their impact.

What common mistakes should be avoided when you design your risk map?
1 / Focus on the threats before having identified the critical assets, the essential ones to the operations of the organization for which we would fear one of the three effects of the C-I-A triad (Confidentiality, Integrity, Availability)
2 / Neglecting the elements of context in which your business operates (business model, business ecosystem, B2B or B2C model, geographic territory, etc.)
3 / Remain too theoretical in terms of the risks identified. Your mapping must address specific risk scenarios, of which the feared loss event is measurable.
4 / Not sufficiently involving the general management and business functions, whereas they are knowledgeable of the company value chain and the critical processes and assets that underpin it.
5 / Be content with a qualitative analysis, based on nominal and ordinal scales, which by nature are subjective. The problem is not the final rendering of the risk mapping but the way the frequency and the impact on losses are estimated.
The limitations of risk mapping
There is an advantage with this type of mapping: it is simple to understand. The colour system is simple to interpret, which is why it is widely used to assess risks, whatever the company’s activities may be. Yet, this simplicity can lean towards being over-simplified and even might be partially false (cf ISO 27005, Annex E 2; How To Measure Anything in Cyber Risk – Doug Hubbard and Richar Seiersen).

However, the world has changed. The risks to companies have greatly evolved, especially with digital technology. Risk mapping as it stands is sorely lacking in precision. It benefits from an association with mathematical methods of quantifying the probability of cyber risks.
Today, the challenge is to assess risks and possible consequences much more accurately, to the point of quantifying impact in financial terms. This is paramount to better managing security (and especially cybersecurity) budgets.
To go further, we advise you to take a look at the FAIR™️(Factor Analysis of Information Risk) methodology.
FAQ : Risk mapping
What is risk mapping?
Risk mapping is a risk management tool in the form of a table. The risks are classified according to their probability and their impact, from lowest to highest.
How can I carry out risk mapping?
Risk mapping usually follows a 4-stage approach: identifying the key activities of the structure, pinning down the risks, assessing their likelihood and impact, and developing detection and protection measures. Nevertheless, this approach varies from one theoretician to another.
Why should you risk map?
Risk mapping brings to light potential threats to the activities or to the very survival of a company. It is a simple and readable graphic tool which helps you make relevant decisions in terms of risk management.

We build scalable solutions to quantify cyber risk in financial terms so organizations can make informed decisions to improve governance and resilience.







