By leveraging technologies such as the Internet of Things (IoT), artificial intelligence (AI), and robotics, smart factories optimize production processes autonomously. These advanced facilities enhance efficiency, reduce waste, reduce cost, and enable real-time data analytics. Simultaneously, responsive supply networks adapt swiftly to changes in demand and supply conditions, ensuring optimal resource allocation and minimizing disruptions. The synergy between digital insights and physical execution is pivotal for transforming manufacturing and logistics into agile, interconnected systems.
The First Industrial Revolution to Industry 4.0
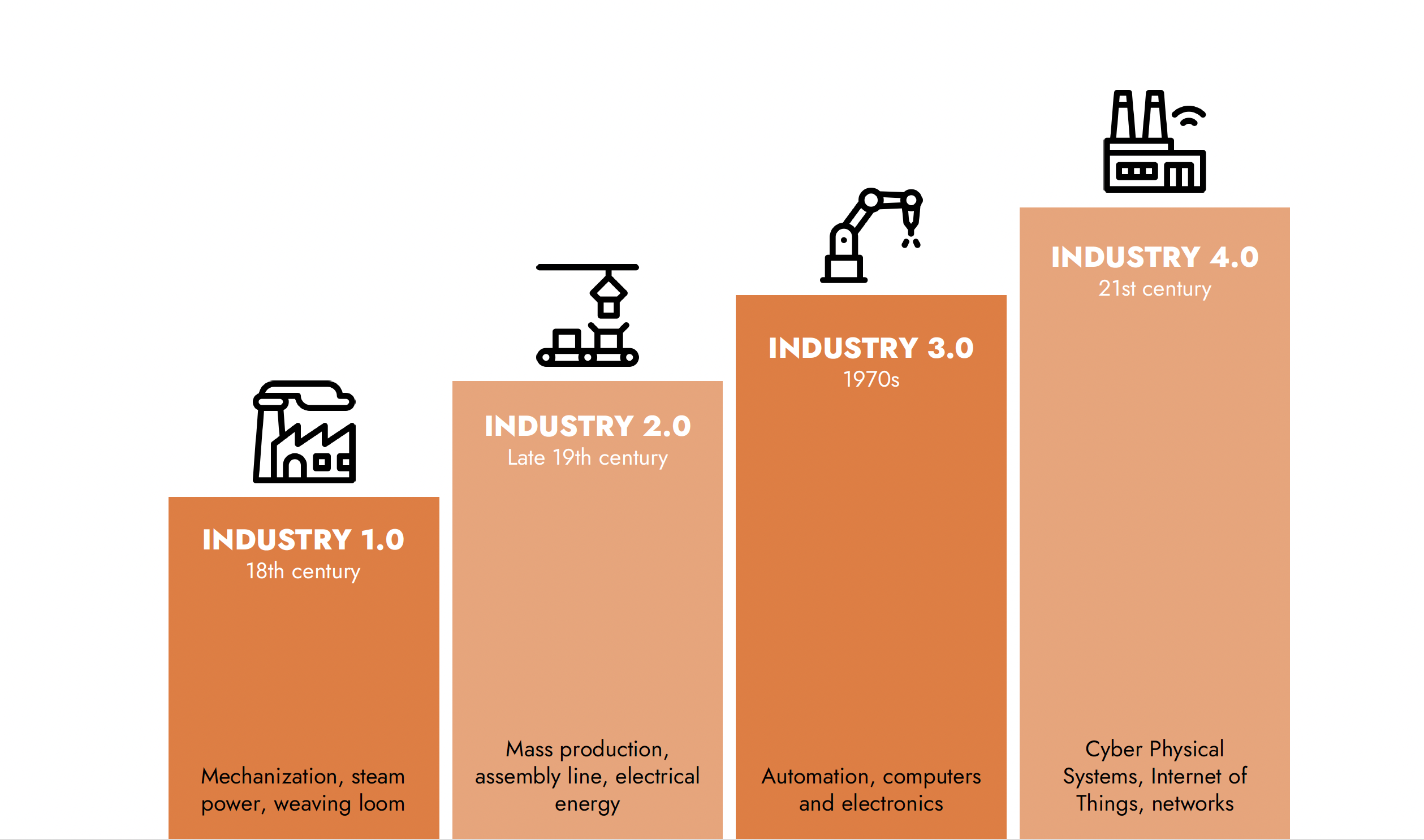
The First Industrial Revolution, which began in 18th century England, saw the mechanization of production and the use of steam power. The Second Industrial Revolution, which began in the late 19th century, introduced mass production and assembly lines, oil and electrical machines, and reduced the need for labor. The Third Industrial Revolution, which began in the 1970s, brought about digitization and automation, with the use of computers and robotics. The Fourth Industrial Revolution, which continues today, introduced smart factories, cyber-physical systems that make use of the Internet of Things (IoT), artificial intelligence (AI), and big data.
The Origins of Industry 4.0
The term “Industrie 4.0,” also known as Industry 4.0 or the Fourth Industrial Revolution, is a neologism that originated in Germany around 2011. It began as a German high-tech strategic initiative to integrate cyber-physical systems, smart machines, storage systems, and production facilities into the manufacturing process. By 2016, the EU had adopted the term and began studying the impact and benefits of developing EU-wide policies to ensure the security and sustainability of cyber-dependent processes for critical services.
Technologies driving Industry 4.0
The concept “Industry 4.0” was born out of a vision to transform the manufacturing sector with advanced digital technologies. The nine technologies that defined its early stage were synergistic. They enabled a new level of automation, connectivity, intelligence, and customization in the manufacturing sector. In 2015, Boston Consulting introduced these technologies as the pillars of the Fourth Industrial Revolution. They are:
- Additive Manufacturing
- Augmented Reality
- Autonomous Robots
- Big Data and Analytics
- The Cloud
- Cybersecurity
- Horizontal and Vertical System Integration
- The Industrial Internet of Things
- Simulation
Disruptive technologies and operational cybersecurity
One of the main drivers of Industry 4.0 is the Industrial Internet of Things (IIoT), which refers to the network of smart devices, sensors, and machines that communicate and exchange data with each other and with humans. The IIoT enables real-time monitoring, control, and optimization of industrial processes, as well as predictive maintenance, asset tracking, and remote management. According to a report by Accenture, the IIoT could add $14.2 trillion to the global economy by 2030.
Another key technology for Industry 4.0 is simulation, which allows businesses to create digital models of their products, processes, and systems, and test them in virtual environments before implementing them in the real world. This helps reduce costs, errors, and time-to-market, as well as improve quality, performance, and sustainability. For example, Siemens uses simulation to design and optimize wind turbines, while Boeing uses it to test new aircraft designs and configurations.
However, the increasing connectivity and complexity of the IIoT and simulation systems also expose them to cyberattacks from malicious threat actors, which can have severe consequences for industrial operations and safety. Cyberattacks can compromise the integrity, availability, and confidentiality of the data and systems, leading to production losses, equipment damage, environmental harm, and even physical injuries.

Learn more about our FAIR-based CRQ Training
Visit our dedicated CRQ Training page for more information about course content and upcoming training sessions.
Operational cybersecurity Challenges
Legacy IT Systems and Interoperability
Many industrial organizations rely on outdated or IT systems that may not support new sensors and communication systems. These legacy systems may also pose security vulnerabilities, performance issues, and maintenance challenges. To overcome these limitations, organizations need to focus on implementing interoperable systems. These changes can entail significant costs, time, and technical expertise. To ensure a smooth transition, there should be system audits and analysis of control gaps that can result of new systems so that production disruptions are minimized and security isn’t compromised.
Costs and Resource Limitations
Adopting disruptive technologies can be a costly and complex undertaking, especially for small and medium-sized enterprises (SMEs) that have limited financial and human resources. Organizations need to invest in hardware, software, infrastructure, training, and consulting services, as well as cope with the potential loss of revenue during the transition period. They also need to balance the short-term costs and benefits with the long-term value and return on investment of their digital transformation initiatives.
Workforce Skills Gap / Reskilling
Industry 4.0 demands a new set of skills and competencies from the workforce, such as data analysis, programming, digital literacy, problem-solving, and creativity. However, many industrial workers lack these skills or need to update and enhance them to keep up with the changing requirements of their jobs. Organizations need to provide continuous education and training opportunities for their employees, as well as recruit and retain new talent with the relevant qualifications and experience.
Change Management
Organizations need to align their vision, strategy, structure, processes, and culture with the new paradigms and opportunities of Industry 4.0. Effective communication is fundamental with internal and external stakeholders, including employees, customers, suppliers, and regulators, to justify digital transformation projects and address any challenges. Clear communication can also help manage any resistance or uncertainty that can arise with the introduction of new technologies.
By addressing these operational risks, organizations can improve their efficiency and build long-term value by harnessing the power of Industry 4.0.
.jpeg)
Cyberattacks on Industry 4.0
Colonial Pipeline Ransomware Attack
The ransomware attack on Colonial Pipeline, which operates the largest fuel pipeline in the United States, disrupted the supply of gasoline and jet fuel to millions of customers across the East Coast in May 2021. The attack was carried out by a group of cybercriminals known as DarkSide. They used a malicious software program to encrypt the data on the company's computer systems and demand payment for the decryption key. The attack forced the company to shut down its entire network of 5,500 miles of pipelines for six days, causing a surge in gas prices, panic buying, and fuel shortages in 17 states. The company reportedly paid 75 bitcoin or about $4.4 million in ransom to the hackers, which was partially recovered by the FBI. The incident exposed the vulnerability of critical infrastructure to cyberattacks and the potential consequences for the economy, national security, and public safety.
Applied Materials Supply Chain Attack
In an announcement in February 2023, Applied Materials, which is one of the world's largest manufacturers of semiconductors, announced that due to a supply chain attack it was facing a $250 million loss in its second quarter sales report. The attack highlighted the interdependence of the global semiconductor supply chain and the need for enhanced cybersecurity measures across the industry, especially for third-party risk management.
As seen in the above examples, the impact of cyberattacks on the supply chain can have long-term and wide-spread consequences.
Balancing External Threats and Internal Risks
While the protection of industrial control systems (ICS) and critical infrastructure from external threats is a vital aspect of industrial cybersecurity, it is not the only one. Organizations also need to address the internal cyber risks.
The human element in cybersecurity
Securing industrial cyber systems goes beyond implementing new technologies; it also includes the critical human element. Employees, if not properly trained, can unintentionally become a conduit for vulnerabilities within the critical infrastructure they operate. Therefore, it is critical to cultivate a culture of cybersecurity awareness at every level of the organization.
This includes educating and training employees at all levels-from operators and engineers on the shop floor to the most senior managers and executives. Training should cover the range of cybersecurity best practices, protocols, and response strategies to effectively combat cyber threats. This includes email hygiene, which plays a critical role in preventing phishing attacks and other forms of social engineering that could compromise the organization's digital assets. Through ongoing education and training, every member of the organization becomes an integral part of the defensive framework, helping to prevent, detect, and respond to cyber incidents and strengthen the organization's overall cybersecurity posture.
By investing in cyber risk awareness training, organizations can enhance their industrial cybersecurity posture and resilience, reduce the likelihood and impact of cyber incidents, and increase their trust and reputation among their customers and partners. Cyber risk training is an opportunity to improve the performance and efficiency of industrial systems and processes.
Conclusion
Industry 4.0 is a transformative paradigm that offers immense opportunities and challenges for industrial organizations. By adopting advanced digital technologies, such as the IIoT, AI, and simulation, organizations can optimize their production processes, supply chains, and data analytics, and gain a competitive edge in the global market. However, they also need to address the cybersecurity and operational risks that arise from the increased connectivity and complexity of these technologies.
Cyberattacks on critical infrastructure can have severe consequences for the economy, national security, and public safety, as well as the reputation and trust of the affected organizations. Therefore, it is essential to implement robust cybersecurity measures, such as risk assessments, system audits, threat intelligence, and incident response plans, to protect the integrity, availability, and confidentiality of the industrial cyber systems. In addition, organizations need to cultivate a culture of cybersecurity awareness among employees as they are a first line of defense against cyber threats. Organizations can empower their workforce to prevent, detect, and respond to cyber incidents, and enhance their industrial cybersecurity posture and resilience by investing in cyber risk awareness training.
C-Risk provides Cyber Risk Quantification training to risk managers, IT and security professionals, CISOs and executives. Our CRQ training will provide you with the tools and processes to analyze cyber risk differently. You will learn how quantification can improve your infosec budget decisions and communication with critical stakeholders. Find out more on our dedicated Training page.

We build scalable solutions to quantify cyber risk in financial terms so organizations can make informed decisions to improve governance and resilience.










