What is ATT&CK?
MITRE ATT&CK® is a knowledge base that helps model the tactics and techniques of cyber adversaries to improve security systems and controls. ATT&CK is an acronym for Adversarial Tactics, Techniques and Common Knowledge. The framework is used to understand and mitigate cybersecurity threats.
It’s essentially a community-driven free, open-source encyclopedia of the behaviors and activities of cybercriminals and threat actors once they breach a system. The ATT&CK framework is based on real-world observations of bad actors. Cyber defenders working in security submit their observations to ATT&CK, which are then added to the repository.
Oftentimes, different security teams will use different terms to describe the same behaviors by threat actors. The ATT&CK framework also provides a common language to help different teams communicate across business units and globally.
We’ll discuss the technical aspects of tactics, techniques and procedures that make up the ATT&CK framework after diving into the origins of the MITRE Corporation and the beginnings of the ATT&CK project.
MITRE’s Defense Origins
The MITRE Corporation was established in 1958 as a military think tank to strengthen US defenses during the Cold War. Its creation was driven by the US Air Force's goal to bridge the academic research community with the defense industry. This initiative emerged within the context of the Cold War and the early days of the Berlin Crisis, when Soviet Premier Nikita Khrushchev demanded that the US, Great Britain and France withdraw their forces from West Berlin.
A key outcome of this public-private collaboration was the development of the Semi-Automatic Ground Environment (SAGE). SAGE was a groundbreaking system that utilized large computers and advanced surveillance equipment to collect data from radar sites across the United States, producing a unified, real-time image of American airspace. SAGE was the nation’s first air defense system – controlling the NORAD response to a possible Soviet air attack.
Today, the MITRE Corporation has expanded its research and development activities, working the fields of defense and intelligence, homeland security, aviation, civil systems, judiciary and healthcare. The ATT&CK framework was the result of these R&D activities.
MITRE FMX is launched in 2010
The MITRE ATT&CK® Framework has its origins as a research project called FMX (Fort Meade eXperiment) in 2010. FMX was a “living lab.” Researchers were given access to a production enclave of MITRE’s corporate network, where they could deploy tools, runs tests and discover ways to detect threats. They were essentially red and blue team exercises The focus of the project was to detect Advanced Persistent Threats (APTs) using data sources and analytic processes using an “assume breach” mentality.
One of the project’s objectives was to improve post-compromise detection of threats using endpoint telemetry and behavioral analytics. FMX categorized observed behavior across real-life adversary groups. They would then use this information when they ran controlled exercises and cyber games within the FMX research environment.
The ATT&CK Model 2013-2024
2013: the first ATT&CK model is created and is focused on the Windows enterprise environment.
2015: The ATT&CK Framework is released to the public based on the Windows enterprise environment. This version includes 96 techniques and 9 tactics.
2017: ATT&CK for Enterprise is released and includes matrices for macOS, Linux and Windows. ATT&CK for Mobile was also released.
2019: ATT&CK for Cloud is included in the Enterprise version.
2020: ATTACK for Industrial Control Systems (ICS) is released.
2024: ATT&CK v15 is released.
ATT&CK Framework
The theory behind ATT&CK is that threat actors have routines, behaviors that are repeated again and again. The TTPs (tactics, techniques and procedures) is a place where it’s easier to catch adversaries because the behaviors of the threat actors don’t change much.
Core Components of ATT&CK
According to the 2020 MITRE paper ATT&CK Design and Philosophy, ATT&CK is a behavioral model that has several core components:
• Tactics: descriptions of the short-term, tactical adversary goals during an attack
• Techniques: description of the general methods used adversaries to achieve tactical goals
• Sub-techniques: more specific description of the means by which adversaries achieve tactical goals at a lower level than techniques
• Documented adversary usage of techniques, their procedures, and other metadata
Ways to Implement ATT&CK
Use Cases
ATT&CK is not just a reference—it’s a living operational tool. Organizations use it for multiple purposes across the security lifecycle:
1. Adversary Emulation
Red Teams replicate known threat actor behaviors (based on ATT&CK TTPs) to test detection and response capabilities.
2. Threat Hunting & Behavioral Analytics
Blue Teams and detection engineers build analytics to identify suspicious activity that maps to ATT&CK techniques.
3. Defensive Gap Assessment
By overlaying security controls on the matrix (via ATT&CK Navigator), teams visualize which adversary techniques are detected, prevented, or uncovered.
4. SOC Maturity Assessment
ATT&CK provides a structured way to measure a SOC’s detection coverage and maturity by tactic (e.g., Lateral Movement or Command & Control).
5. Cyber Threat Intelligence (CTI) Enrichment
CTI teams map threat groups and campaigns to specific ATT&CK techniques, linking new indicators or malware to known behaviors.
Tools and Platforms Supporting MITRE ATT&CK®
MITRE and the broader community provide several tools to make ATT&CK actionable:
🔹 ATT&CK Navigator – visualize coverage and create custom heatmaps for your environment.
🔹 MITRE CAR (Cyber Analytics Repository) – ready-to-use analytics and queries for detecting ATT&CK techniques.
🔹 ATT&CK Workbench – host a private instance of ATT&CK, customize groups and campaigns, and manage internal knowledge bases.
SIEM and EDR Integrations:
- Splunk Enterprise Security – built-in ATT&CK dashboards and content updates.
- IBM QRadar – mapping rules and investigation workflows by tactic.
- Elastic Security – ATT&CK-aligned detections and timeline visualizations.
- Microsoft Sentinel – analytic rules and workbooks aligned to ATT&CK.
These integrations ensure that alerts are automatically contextualized within the ATT&CK matrix, streamlining investigations and reporting.

Contact C-Risk
Want to evaluate your organization’s maturity against MITRE ATT&CK techniques? Our C-Risk experts can help you implement a defense strategy aligned with ATT&CK best practices and risk-based priorities.
Integrating ATT&CK Into a Cybersecurity Strategy
A mature cybersecurity program uses ATT&CK not only for post-incident analysis but for strategic defense design.
1. Identify Relevant Threats
Analyze threat intelligence to understand which APT groups and TTPs target your industry.
2. Assess Exposure and Critical Assets
Map your most valuable systems and data—those most likely to be exploited—and identify entry points or dependencies.
3. Prioritize Techniques
Use a risk-based approach: evaluate likelihood × impact and focus on controls that address multiple techniques simultaneously.
4. Strengthen Preventive Controls
Implement hardening baselines (CIS), segmentation, privilege management, patching, and cloud configuration management.
5. Enhance Detection & Response
Develop SIEM use cases and EDR/XDR detections aligned with ATT&CK. Deploy honeytokens and deception technologies to catch lateral movement.
6. Continuously Improve
Run red/blue/purple team exercises, simulate ATT&CK scenarios, and feed lessons learned back into your detection and playbooks.
By adopting ATT&CK as a unifying layer across prevention, detection, and response, organizations move toward adaptive, intelligence-driven defense.
Conclusion
The MITRE ATT&CK® Framework is far more than a catalog of attacker techniques—it’s a strategic foundation for building resilient, behavior-based security programs.
By embedding ATT&CK into threat modeling, incident response, and risk management, organizations transition from static defenses to dynamic, proactive cybersecurity.
FAQ
How does MITRE ATT&CK differ from the Cyber Kill Chain?
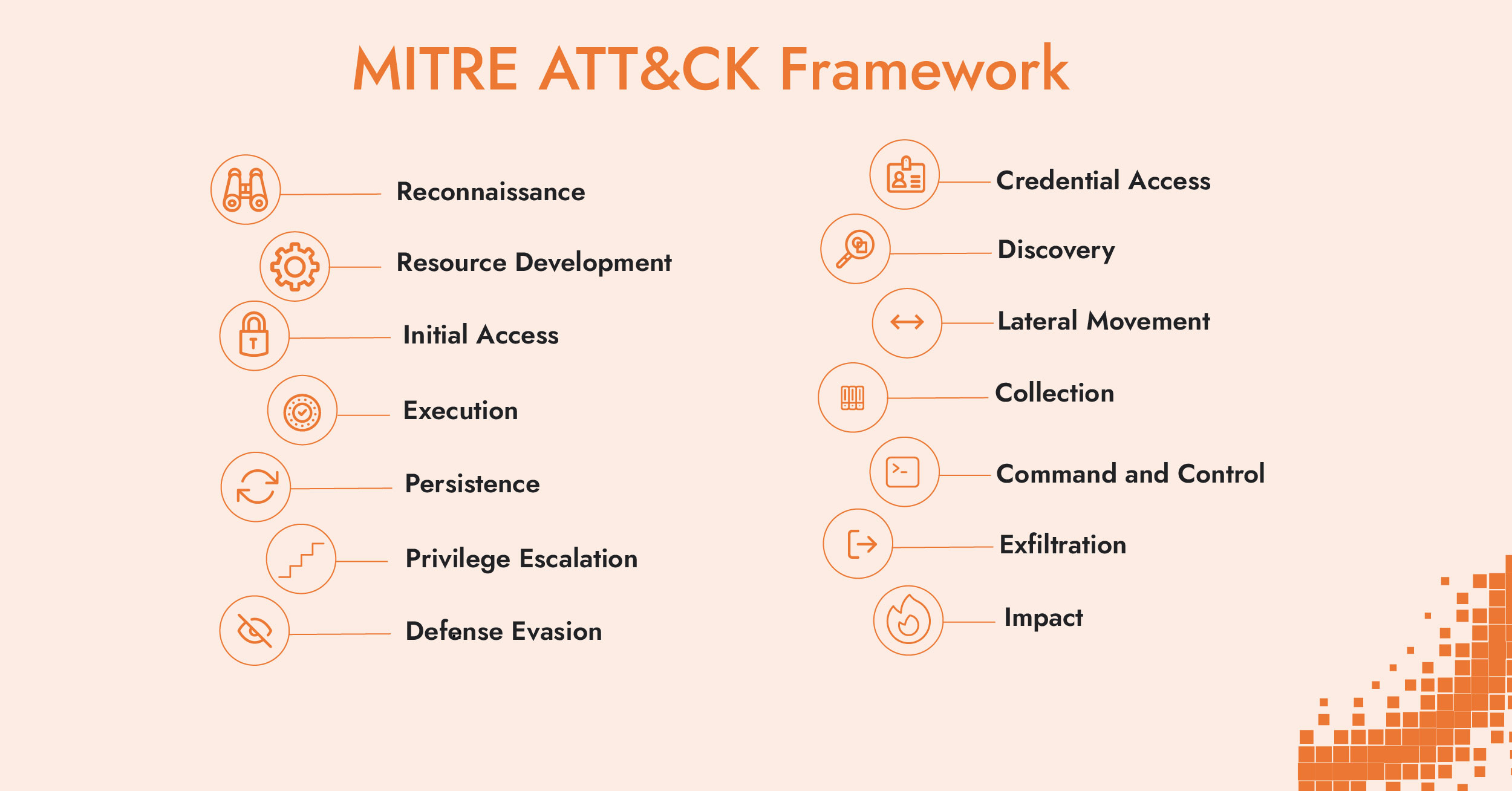
The Cyber Kill Chain describes attacks as a linear sequence of seven steps. ATT&CK is more flexible and granular, representing 14 tactics and hundreds of techniques that may occur non-linearly or repeatedly. It focuses on post-compromise behavior.
Can MITRE ATT&CK be used in cloud or IoT environments?
Yes. MITRE has extended ATT&CK to cover Cloud (AWS, Azure, GCP, SaaS) and Industrial Control Systems (ICS), ensuring its relevance for modern hybrid architectures.
How should a small organization get started with ATT&CK?
Start small: identify the 5–10 techniques most used against your sector, map your current controls in ATT&CK Navigator, and prioritize quick wins like centralized logging and configuration hardening. Expand gradually as maturity grows.

We build scalable solutions to quantify cyber risk in financial terms so organizations can make informed decisions to improve governance and resilience.







