Cybercriminals: What Do You Need to Know?
Cybercriminals operate in a constantly evolving digital ecosystem, targeting individuals, businesses, and public institutions to steal data, disrupt operations, or generate illicit profit. While their technical skills vary widely, they share a common ability to exploit weaknesses in computer systems, human behavior, or organizational processes. Understanding their profile is not about stereotyping attackers, but rather about recognizing the patterns that shape modern cybercrime.
A cybercriminal can be defined as an individual or group that uses digital tools, malicious techniques, or unauthorized access to engage in illegal activities. These activities range from ransomware attacks and data breaches to financial fraud, identity theft, and denial-of-service campaigns designed to overwhelm systems.
Studying their profile offers valuable insight into how they think and operate. Some actors focus exclusively on stealing personal information to sell on the dark web, while others pursue political, ideological, or economic objectives. Their level of organization also differs significantly: some are isolated amateurs testing their skills, while others take part in highly structured criminal networks comparable to traditional organized crime.
Understanding who these attackers are helps identify the threats most likely to affect an organization. It clarifies their preferred targets, techniques, and methods of escalation inside networks. Most importantly, these insights enable companies to anticipate malicious activities rather than react to them. As cybercrime becomes increasingly commoditized - with ready-made malware kits, exploit marketplaces, and “cybercrime-as-a-service” models - knowing your adversary is no longer optional; it is a core element of modern cybersecurity resilience.
Why Study a Cybercriminal’s Profile?
Understanding the profile of a cybercriminal is a strategic priority for any organization aiming to strengthen its cybersecurity posture. Cyberattacks increasingly blend technical sophistication with social engineering, making it essential to anticipate an attacker’s behavior rather than simply react to incidents.
Awareness and Preparation
Studying cybercriminals helps organizations understand how attackers identify vulnerable targets, gain initial access, and escalate privileges within networks. This knowledge strengthens awareness programs and reduces the effectiveness of phishing attempts, credential theft and other manipulative techniques. It also enables more realistic incident response exercises, allowing teams to rehearse scenarios based on genuine criminal behavior rather than generic simulations.
Developing Effective Defense Strategies
Understanding a cybercriminal’s motivations, whether financial, ideological or opportunistic, helps organizations design more robust and targeted defense mechanisms. For instance:
- Companies exposed to ransomware attacks can focus on strengthening backup resilience and segmentation.
- Organizations handling large volumes of personal data can prioritize detection systems that monitor abnormal access or exfiltration attempts.
- Entities at risk of espionage can invest in advanced threat monitoring and behavioral analytics.
Ultimately, profiling attackers enables cybersecurity teams to align their defenses with the real-world tactics used by malicious actors. Instead of a one-size-fits-all approach, organizations can build tailored strategies that proactively limit opportunities for intrusion. In a landscape where cybercrime evolves rapidly and criminal activities scale through automation, this level of insight is indispensable.
Types of Cybercriminals
Cybercriminals are not a homogeneous group. They differ in motivation, skill level, resources, and organizational structure. Understanding these categories helps organizations anticipate the type of cybercrime they are most likely to face - whether espionage, ransomware attacks, data theft, or large-scale disruption.
Cyber Spies
Cyber spies (often linked to state-sponsored groups) focus on gathering highly sensitive or strategic information. Their targets include government agencies, research institutions, and corporations involved in defense, energy, or advanced technologies.
These actors rely on stealth, advanced exploits, and long-term infiltration, prioritizing persistence over disruption. Their operations can remain undetected for months while they exfiltrate intellectual property or confidential data.
Organized Criminal Groups
Organized cybercrime groups function like traditional criminal organizations but operate primarily in the digital world. They run scalable illegal businesses: selling stolen data, trading malware kits, harvesting credit card details, or operating fraudulent online platforms.
Their attacks are systematic and financially driven, relying on a network of developers, recruiters, money launderers, and infrastructure suppliers. These groups are responsible for a significant portion of global data breaches and financial fraud.
Ransomware Authors
Ransomware authors design, distribute, or sell malicious software that encrypts victims’ data and demands payment for decryption. Some operate directly, while others offer “Ransomware-as-a-Service” to less skilled criminals.
Their attacks often combine phishing, vulnerabilities exploitation, and lateral movement inside networks. The objective is straightforward: maximize financial gain by paralyzing operations and extorting organizations desperate to recover their personal information and business data.
Methods and Tools Used by Cybercriminals
Cybercriminals rely on a wide range of tools and techniques to exploit vulnerabilities, steal personal data, and infiltrate computer systems. Understanding these methods allows organizations to strengthen their defenses and detect malicious activities earlier. While their sophistication varies, most attacks fall into a few key categories.
Hacking Tools
Cybercriminals frequently use specialized software designed to scan, infiltrate or manipulate systems. Common examples include:
- Password-cracking programs capable of breaking weak or reused credentials.
- Keyloggers that record keystrokes to steal login details or financial information.
- Remote Access Trojans (RATs) enabling attackers to take control of a device without the user’s knowledge.
- Packet sniffers that intercept network traffic, including unencrypted personal or financial data.
Some of these tools are freely available online, while others are traded on the dark web, contributing to the democratization of cybercrime.
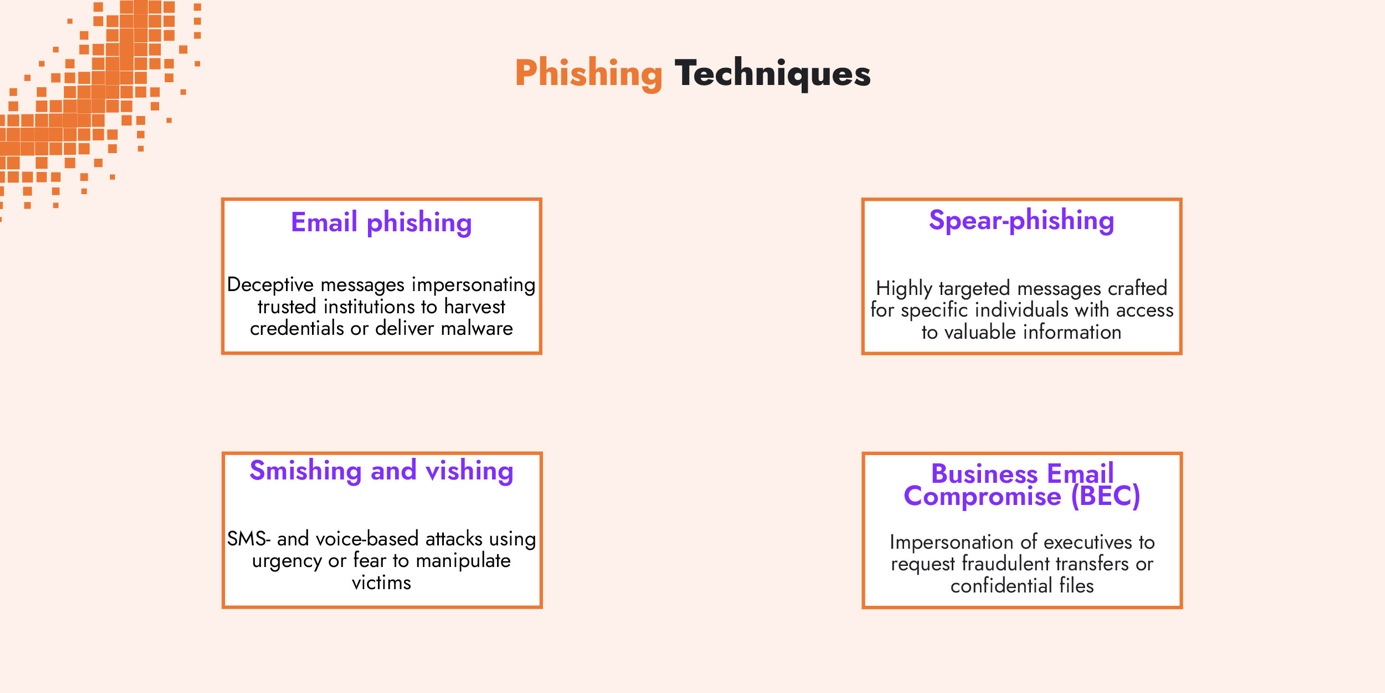
Phishing Techniques
Phishing remains one of the most effective and widespread methods used by cybercriminals. By exploiting human behavior, attackers gain access to systems without having to break through technical safeguards.
Key phishing approaches include:
- Email phishing: deceptive messages impersonating trusted institutions to harvest credentials or deliver malware.
- Spear-phishing: highly targeted messages crafted for specific individuals with access to valuable information.
- Smishing and vishing: SMS- and voice-based attacks using urgency or fear to manipulate victims.
- Business Email Compromise (BEC): impersonation of executives to request fraudulent transfers or confidential files.
These attacks often serve as an entry point for ransomware, data theft or network compromise.
Exploits and Vulnerabilities
Cybercriminals also take advantage of flaws in software, systems or network architecture. These vulnerabilities can be newly discovered (zero-days) or unpatched weaknesses already known to the public, a trend regularly emphasized by CISA in its public vulnerability bulletins.
Examples include:
- Exploiting outdated operating systems or applications.
- Leveraging insecure configurations such as exposed databases or weak authentication policies.
- Using automated scanning tools to detect vulnerable servers across the internet.
- Taking advantage of supply chain weaknesses to infiltrate multiple organizations at once.
Successful exploitation enables criminals to gain access to sensitive systems, escalate privileges, and exfiltrate stolen data without immediate detection.
The Psychology of the Cybercriminal
Behind every cyberattack lies a set of motivations that shape how cybercriminals operate, the targets they choose, and the risks they are willing to take. Understanding these psychological drivers helps organizations anticipate potential threats and tailor their cybersecurity strategy accordingly. While motivations can overlap, most cybercriminals tend to fall into one or more of the following categories.
Profit-Seeking
Financial gain remains the most common motivation behind cybercrime. Criminals seeking profit focus on activities that generate immediate or scalable revenue, such as:
- Stealing and selling personal information or credit card details
- Running ransomware campaigns to extort companies
- Trafficking illegal information or offering cybercrime-as-a-service
- Monetizing stolen data through online marketplaces
These actors prefer high-impact, low-risk operations and often participate in well-structured criminal ecosystems.


Strengthen your cybersecurity posture
Cybercriminals are evolving - your defences should too. Discover how C-Risk helps organisations assess digital risks, reduce exposure, and build resilient security strategies.
Need for Recognition
Some cybercriminals are motivated by status, visibility, or a desire to demonstrate their technical superiority. This profile is more common among younger or less experienced attackers who seek validation from online communities.
Their behavior may include:
- Defacing websites to showcase their “signature”
- Publicly leaking data to gain notoriety
- Demonstrating new exploits to impress peers
- Attempting risky intrusions simply for the challenge
Although not always financially driven, their actions can cause significant reputational and operational damage.
Ideological Motivations
Ideologically driven cybercriminals, including hacktivists, use digital tools to support political, environmental, religious or social causes. Their priority is influence rather than profit.
Typical activities include:
- Exposing confidential information to denounce an organization
- Launching DDoS attacks to disrupt perceived adversaries
- Spreading propaganda or manipulating public opinion
- Targeting institutions that conflict with their values
These attackers may act independently or as part of loosely organized activist groups.
Conclusion
Understanding the profile of a cybercriminal is essential to building effective, proactive cybersecurity. By identifying their motivations, preferred targets, and attack methods, organizations can adjust their defenses to reduce exposure and respond more efficiently to emerging threats. As cybercrime continues to evolve, a strategic and informed approach is key to protecting systems, safeguarding personal data, and maintaining business resilience.
FAQ
What is the primary objective of a cybercriminal?
Most cybercriminals seek financial gain, targeting personal data, business information, or digital infrastructure to monetise it. Others act for ideological or reputational motives
How do cybercriminals typically gain access to systems?
They often rely on phishing, exploiting vulnerabilities, credential theft, or misconfigured systems. Human error remains one of the most common entry points
What can organizations do to prevent cyberattacks?
They can strengthen access controls, apply regular patches, deploy behavior-based detection tools, train employees, and conduct periodic cybersecurity risk assessments.

We build scalable solutions to quantify cyber risk in financial terms so organizations can make informed decisions to improve governance and resilience.






