What About Cyber Awareness?
Definition of Cyber Awareness
Cyber awareness encompasses the knowledge, skills, and behaviors necessary to protect digital assets and personal information from cyber threats. It represents a holistic understanding of how cyber security risks manifest in daily digital interactions and the proactive measures required to mitigate them.
At its core, cyber awareness involves recognizing potential threats such as phishing emails, suspicious links, and social engineering attempts. It extends beyond mere technical knowledge to include behavioral changes that reduce vulnerability to attacks. This includes understanding how human error contributes to security breaches and developing habits that minimize risk exposure.
The concept integrates multiple dimensions of digital safety:
- Recognition of common attack vectors and threat indicators
- Understanding of data protection principles and privacy rights
- Knowledge of organizational security policies and procedures
- Ability to respond appropriately to security incidents
- Continuous adaptation to evolving threat landscapes
The Importance of Adopting Safe Digital Behaviors
Safe digital behaviors form the practical application of cyber awareness knowledge. These behaviors range from creating strong passwords and enabling multi-factor authentication to scrutinizing email attachments and maintaining updated software.
The adoption of these behaviors requires a fundamental shift in how individuals perceive their role in cybersecurity. Rather than viewing security as solely an IT responsibility, cyber awareness promotes a culture where every user becomes an active participant in organizational defense.
Critical safe behaviors include:
- Verifying sender authenticity before sharing personal information
- Regular password updates and unique credentials for different accounts
- Careful management of social media privacy settings
- Skeptical evaluation of unsolicited communications
- Proper handling and classification of sensitive data
Why is Cyber Awareness Crucial Today?
Rise in Cyberattacks and Data Breaches
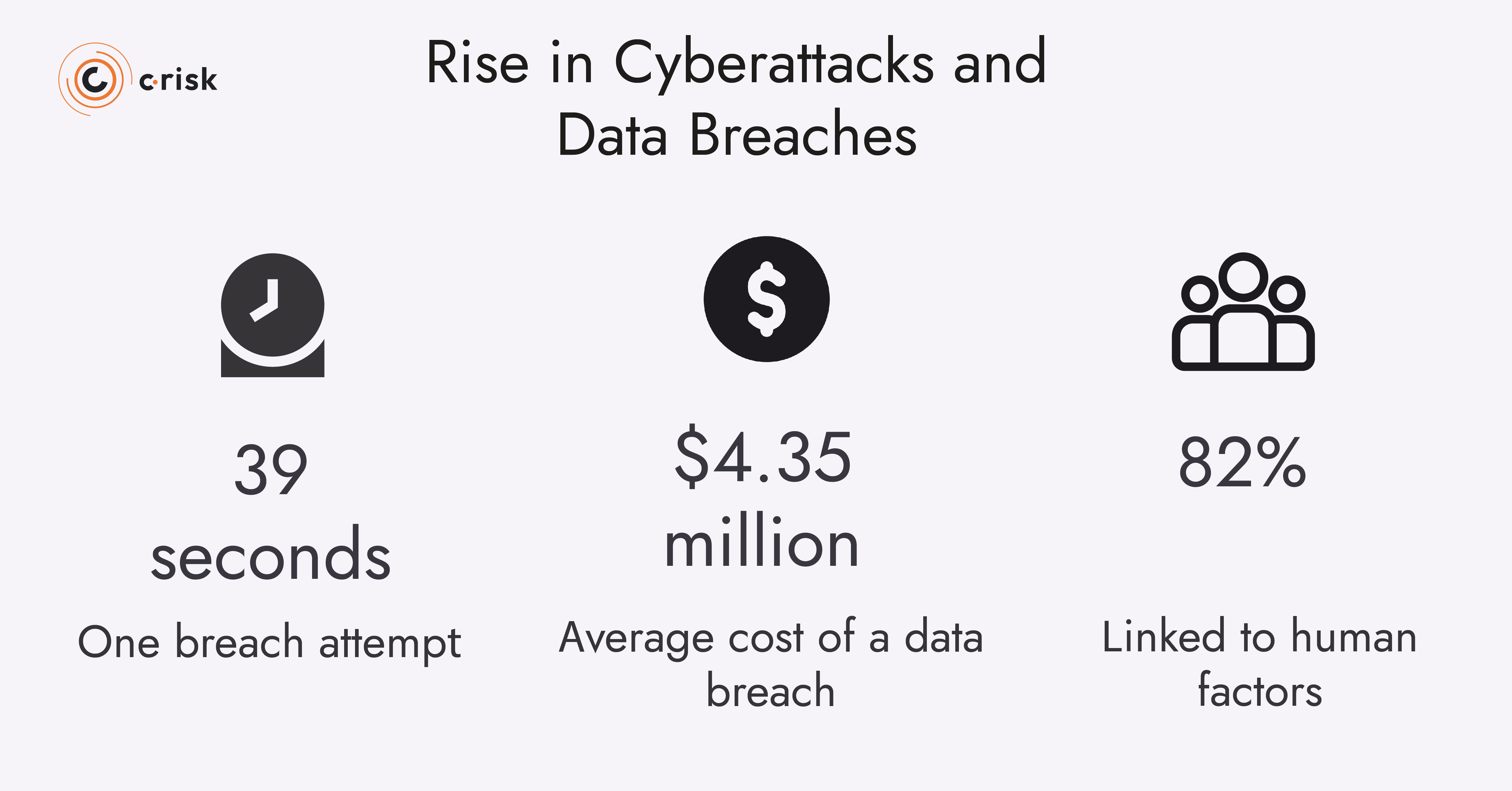
The cybersecurity landscape has witnessed an unprecedented surge in cyber attacks over recent years. According to industry reports, organizations face attempted breaches every 39 seconds on average, with successful attacks causing devastating financial and reputational damage.
The sophistication of modern attacks has evolved dramatically. Threat actors now employ:
- Advanced persistent threats (APTs) that remain undetected for months
- Ransomware-as-a-Service (RaaS) platforms democratizing cybercrime
- AI-powered attack tools that adapt to defensive measures
- Supply chain attacks targeting trusted third-party relationships
- Zero-day exploits leveraging previously unknown vulnerabilities
This escalation makes cybersecurity awareness essential for every organization, regardless of size or industry. The average cost of a data breach now exceeds $4.35 million globally, with human-related factors contributing to 82% of breaches.
Proliferation of Connected Devices (IoT)
The Internet of Things (IoT) revolution has exponentially expanded the attack surface available to cybercriminals. With billions of connected devices ranging from smart home assistants to industrial control systems, each represents a potential entry point for malicious actors.
IoT security challenges include:
- Default or weak credentials on devices
- Irregular security updates and patch management
- Lack of visibility into device communications
- Integration with critical business systems
- Consumer devices on corporate networks
This proliferation demands heightened security awareness training that addresses not just traditional computing devices but the entire spectrum of connected technologies users interact with daily.
The Significance of Personal Data and Its Value on the Black Market
Personal data has become the new currency of the digital underground. Personal information ranging from credit card numbers to medical records commands premium prices on dark web marketplaces.
Data valuation on black markets reveals:
- Complete identity packages selling for $1,000-$2,000
- Credit card information trading at $5-$110 per card
- Medical records fetching up to $1,000 per record
- Corporate email credentials valued at $50-$500
- Social media accounts selling for $1-$300
This economic incentive drives continuous innovation in attack methodologies, making email security and data protection paramount concerns for individuals and organizations alike.
Financial, Reputational, and Legal Consequences of Security Breaches
The impact of inadequate cyber awareness extends far beyond immediate financial losses. Organizations face multifaceted consequences including:
Financial impacts encompass:
- Direct costs of incident response and recovery
- Business disruption and lost productivity
- Customer compensation and credit monitoring services
- Increased insurance premiums
- Technology infrastructure upgrades
Reputational damage manifests through:
- Loss of customer trust and loyalty
- Negative media coverage and public perception
- Competitive disadvantage in the marketplace
- Difficulty attracting talent and partners
- Long-term brand value depreciation
Legal ramifications include:
- Regulatory fines under GDPR, CCPA, and other frameworks
- Class-action lawsuits from affected customers
- Contractual penalties for service level agreement violations
- Director and officer liability claims
- Mandatory disclosure requirements
Key Components of Cyber Awareness
Education and Training
Effective awareness training programs form the backbone of organizational cyber resilience. These programs must evolve beyond annual compliance checkboxes to become engaging, continuous learning experiences that resonate with diverse audiences.
Modern education approaches incorporate:
- Microlearning modules delivering bite-sized content
- Role-based training tailored to specific job functions
- Gamification elements increasing engagement and retention
- Real-world scenarios reflecting current threat landscapes
- Interactive workshops fostering collaborative learning
Successful programs ensure employees understand not just what to do, but why it matters. This contextual understanding transforms compliance-driven behaviors into genuine security consciousness.
Attack Simulations
Hands-on experience through simulated attacks provides invaluable learning opportunities. These controlled exercises expose users to realistic threat scenarios without actual risk, building muscle memory for appropriate responses.
Simulation methodologies include:
- Phishing simulations testing email vigilance
- Vishing (voice phishing) exercises via phone calls
- Physical security tests evaluating tailgating and device security
- Social engineering scenarios on social media platforms
- USB drop tests assessing removable media policies
These simulations generate metrics enabling organizations to:
- Identify vulnerable departments or roles
- Measure training effectiveness over time
- Customize future education initiatives
- Demonstrate security program ROI
Regular Updates
The dynamic nature of cyber threats demands continuous knowledge refresh. Static, outdated training quickly becomes irrelevant as threat actors develop new tactics, techniques, and procedures (TTPs).
Update mechanisms should address:
- Emerging threat intelligence and attack trends
- New regulatory requirements and compliance standards
- Technology changes introducing fresh vulnerabilities
- Lessons learned from industry incidents
- Evolution of organizational risk profiles
Leading security agency frameworks recommend monthly threat briefings, quarterly training updates, and immediate alerts for critical emerging threats.
Incident Response
Knowing how to react when security incidents occur minimizes damage and accelerates recovery. Effective incident response training empowers users to become first responders in the security chain.
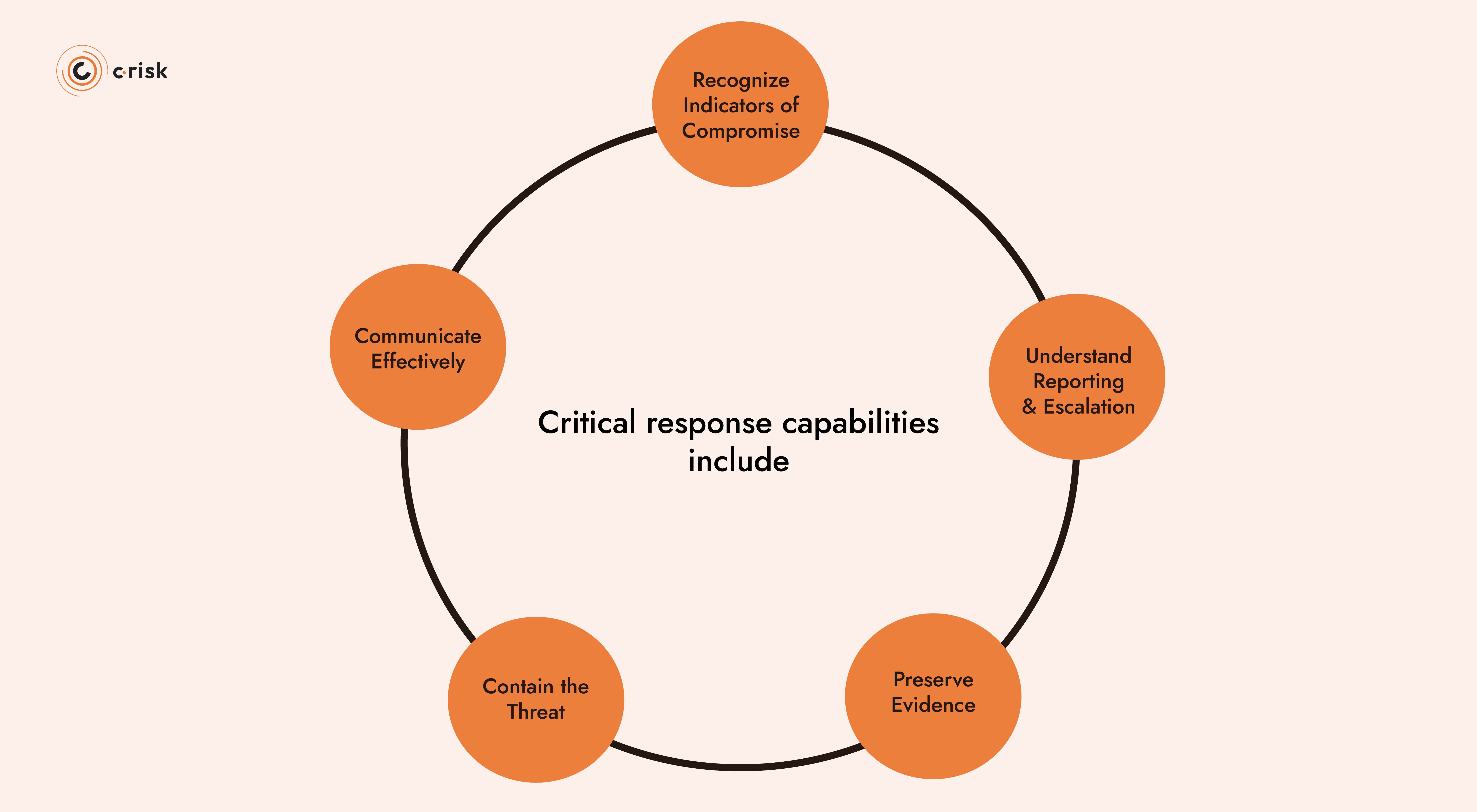
Critical response capabilities include:
- Recognizing indicators of compromise
- Understanding reporting procedures and escalation paths
- Preserving evidence for forensic investigation
- Containing threats to prevent lateral movement
- Communicating effectively during crisis situations
Organizations implementing comprehensive incident response training report 30% faster threat containment and 25% reduction in breach costs compared to those without such programs.
Challenges in Implementing Cyber Awareness
Difficulty in Maintaining Ongoing Training
Sustaining engagement in security awareness training over time presents significant challenges. Initial enthusiasm often wanes as training becomes routine, leading to decreased participation and effectiveness.
Common obstacles include:
- Training fatigue from repetitive content
- Competing priorities and time constraints
- Lack of management support and reinforcement
- Insufficient resources for program maintenance
- Difficulty measuring behavioral change
Overcoming these challenges requires creative approaches such as:
- Rotating training formats and delivery methods
- Integrating security into existing business processes
- Leveraging peer champions and success stories
- Providing tangible incentives for participation
- Demonstrating clear connections to personal benefits
Combatting User Complacency or Disinterest
Many users view cybersecurity as an IT problem rather than a shared responsibility. This disconnect breeds complacency that undermines even well-designed awareness programs.
Factors contributing to disinterest include:
- Perception that "it won't happen to me"
- Technical jargon creating barriers to understanding
- Lack of relevance to daily job functions
- Absence of visible consequences for poor practices
- Overwhelming complexity of security requirements
Effective strategies for engagement involve:
- Personalizing risks to individual roles and responsibilities
- Using plain language and relatable examples
- Highlighting real-world incidents and their impacts
- Creating positive reinforcement for secure behaviors
- Simplifying security processes wherever possible
The Increasing Complexity of Cyberattacks
As cyber threats grow more sophisticated, keeping awareness training current and comprehensive becomes increasingly difficult. Advanced attacks often bypass traditional security measures, requiring nuanced understanding beyond basic awareness.
Complexity challenges manifest in:
- Multi-stage attacks requiring pattern recognition
- Social engineering tactics exploiting psychological vulnerabilities
- Technical attacks masquerading as legitimate processes
- Supply chain compromises affecting trusted relationships
- Nation-state actors using advanced persistent threats
Organizations must balance comprehensive coverage with avoiding information overload that paralyzes users rather than empowering them.
Striking a Balance Between Awareness and Paranoia
Excessive security messaging can create counterproductive paranoia that impedes business operations. Users overwhelmed by constant warnings may either ignore all alerts or become paralyzed by fear of making mistakes.
Finding equilibrium requires:
- Risk-based prioritization of security messages
- Clear differentiation between critical and routine alerts
- Positive framing emphasizing empowerment over fear
- Practical guidance rather than abstract warnings
- Recognition that perfect security is unattainable
The goal is cultivating healthy skepticism without creating an atmosphere of distrust that damages collaboration and productivity.

Partner with C-Risk to develop a cyber awareness program that aligns with your unique risk profile and business objectives.
By implementing the practical steps outlined in this guide and leveraging professional expertise in security awareness design, organizations can build resilient defenses that protect against both current and future cyber threats.
Practical Steps to Strengthen Cyber Awareness
Establishing a Security Culture from Day One
Building robust cybersecurity awareness begins with embedding security into organizational DNA from inception. New employee onboarding represents a critical opportunity to establish security as a core value rather than an afterthought.
Foundational elements include:
- Security orientation during first-day activities
- Clear communication of security policies and expectations
- Assignment of security mentors for new hires
- Integration of security into job descriptions
- Regular reinforcement through leadership messaging
Organizations with strong security cultures report 52% fewer security incidents than those treating security as a compliance requirement.
Using Tools and Platforms to Facilitate Training
Modern security solutions leverage technology to deliver engaging, effective awareness training at scale. These platforms provide automated delivery, tracking, and reporting capabilities that reduce administrative burden while improving outcomes.
Leading platforms offer:
- Learning management systems (LMS) with security modules
- Automated phishing simulation tools
- Video-based training libraries
- Mobile-friendly microlearning applications
- Virtual reality security scenarios
Integration with existing infrastructure enables:
- Single sign-on reducing password fatigue
- Automated enrollment based on role changes
- Performance tracking linked to HR systems
- Customized content matching organizational needs
- Multi-language support for global teams
Hosting Awareness Events or Workshops
Interactive events create memorable learning experiences that transcend traditional training formats. These gatherings foster community engagement while addressing security topics in accessible, enjoyable ways.
Successful event formats include:
- Cybersecurity Awareness Month activities
- "Lunch and Learn" sessions on trending topics
- Capture-the-flag competitions for technical staff
- Security escape rooms for team building
- Guest speakers sharing real-world experiences
Events generate enthusiasm by:
- Breaking routine training monotony
- Creating social learning opportunities
- Recognizing security achievements publicly
- Building cross-functional relationships
- Demonstrating organizational commitment to security
Championing the Establishment of Cybersecurity Champions
Security champion programs distribute awareness responsibilities throughout the organization, creating networks of engaged advocates who reinforce security messages at the grassroots level.
Champion programs succeed through:
- Voluntary participation ensuring genuine interest
- Regular training keeping champions current
- Formal recognition of champion contributions
- Dedicated communication channels for champions
- Authority to influence departmental practices
These distributed networks multiply awareness impact by providing:
- Peer-to-peer security guidance
- Localized threat intelligence sharing
- Early warning of emerging risks
- Feedback on training effectiveness
- Cultural change from within teams
Champions report increased job satisfaction from contributing to organizational security while developing valuable skills for career advancement.
Conclusion
Cyber awareness represents the critical human layer in modern cybersecurity defense strategies. As threats continue evolving in sophistication and frequency, organizations must invest in comprehensive awareness programs that transform users from potential vulnerabilities into active security participants. The journey from basic compliance training to genuine security culture requires sustained commitment, creative engagement strategies, and continuous adaptation to emerging threats. By implementing the practical steps outlined in this guide and leveraging professional expertise in security awareness design, organizations can build resilient defenses that protect against both current and future cyber threats. Partner with C-Risk to develop a cyber awareness program that aligns with your unique risk profile and business objectives.
FAQ
How often should cyber awareness training be conducted for maximum effectiveness?
While annual training meets minimum compliance requirements, research shows monthly touchpoints significantly improve security outcomes. Effective programs combine quarterly comprehensive training sessions with monthly microlearning modules, weekly security tips, and immediate alerts for critical threats. This continuous engagement maintains security top-of-mind without causing training fatigue. Organizations implementing this cadence report 45% better phishing detection rates and 60% faster incident reporting compared to annual-only training approaches.
What metrics should organizations track to measure cyber awareness program success?
Key performance indicators for cyber awareness include phishing simulation click rates, incident reporting times, security policy violations, and training completion rates. Advanced metrics encompass behavior change indicators like password strength improvements, reduction in shadow IT usage, and increased security tool adoption. Qualitative measures through security culture surveys provide insights into attitude shifts and perceived program value. Leading organizations also track correlation between awareness metrics and actual security incidents to demonstrate program ROI.
How can small businesses implement effective cyber awareness without dedicated security teams?
Small businesses can leverage managed security awareness services that provide enterprise-grade training at accessible price points. Cloud-based platforms offer automated training delivery, phishing simulations, and reporting without requiring technical expertise. Industry associations often provide free resources tailored to specific sectors. Partnering with managed security service providers (MSSPs) can provide access to security expertise on-demand. The key is starting with basics like password management and phishing recognition, then gradually expanding coverage as resources permit.

We build scalable solutions to quantify cyber risk in financial terms so organizations can make informed decisions to improve governance and resilience.






