The Foundation of ISMS
An ISMS (Information Security Management System) is not just a collection of technical controls, it’s a comprehensive framework that integrates people, processes, and technology to safeguard an organization’s information assets. Its purpose is to ensure the confidentiality, integrity, and availability of data, three fundamental pillars often referred to as the CIA triad.
At its core, an ISMS enables an organization to identify, manage, and reduce information security risks in a structured and consistent way. Rather than reacting to incidents, it encourages a proactive approach — anticipating vulnerabilities, assessing risks, and implementing appropriate security measures.
The Principles of Information Security
The ISMS approach is grounded in three key principles:
- Confidentiality: ensuring that information is accessible only to those authorized to view it.
- Integrity: maintaining the accuracy and completeness of information throughout its lifecycle.
- Availability: ensuring that information and systems are accessible when needed.
These principles extend beyond technical measures. They encompass organizational culture, employee behavior, and management commitment, ensuring that security becomes part of everyday business operations rather than a one-time project.
ISO/IEC 27001: The International Standard
The ISO/IEC 27001 standard serves as the cornerstone of ISMS implementation. It defines the requirements for establishing, maintaining, and continually improving an information security management system. Organizations adopting this standard benefit from:
- A structured framework for managing risks and controls.
- Compliance alignment with international best practices.
- Improved stakeholder trust through certification and demonstrable governance.
By aligning with ISO/IEC 27001, organizations can transition from ad hoc security measures to a systematic, auditable, and scalable approach to information protection.
Key Steps to Implementing an Effective ISMS
Implementing an Information Security Management System (ISMS) is not a one-time technical deployment but a structured, continuous process. It requires a methodical approach that aligns security objectives with business goals, ensuring that every measure contributes to the protection of information assets and the organization’s resilience as a whole.
Below is a step-by-step roadmap to help guide a successful implementation.
1. Risk Analysis: Identify and Assess Information Security Risks
Every ISMS begins with a comprehensive risk assessment. This involves identifying potential threats to your information systems — from cyberattacks and human error to supply-chain vulnerabilities — and evaluating their likelihood and potential impact.
The objective is not to eliminate all risks (which is impossible) but to understand and prioritize them, allowing the organization to make informed decisions on where to allocate resources most effectively.
A strong risk analysis provides the foundation for all subsequent security decisions. Frameworks such as ISO 31000 or EBIOS Risk Manager can help structure this process, ensuring consistency and traceability.
2. Security Policy Definition: Establish Clear Governance
Once risks have been analyzed, the next step is to develop a security policy that clearly defines the organization’s information security objectives, principles, and responsibilities.
This document serves as a strategic compass, aligning management commitment and employee behavior with the ISMS goals. It should articulate:
- The scope and objectives of the ISMS.
- The governance structure and key roles.
- The organization’s stance on risk tolerance and control priorities.
A well-crafted security policy ensures that all security initiatives are consistent, measurable, and business-driven rather than reactive or fragmented.
3. Select Control Measures: Choose the Right Defenses
Based on the identified risks and the security policy, organizations must select appropriate control measures. ISO/IEC 27001 Annex A offers a catalogue of controls covering areas such as:
- Access control and identity management.
- Data encryption and system hardening.
- Physical and environmental protection.
- Supplier and third-party management.
- Incident response and business continuity.
The chosen measures should be proportionate to the level of risk, ensuring both protection and operational efficiency.
4. Control Implementation: Deploy and Integrate
After selecting controls, the focus shifts to implementation. This involves configuring technical solutions, updating internal processes, and training employees to ensure seamless integration across the organization.
Effective deployment requires collaboration between IT, compliance, HR, and management teams, as information security touches every operational layer. The key is to make security practices both practical and repeatable — embedding them in daily workflows rather than treating them as isolated compliance tasks.
5. Training and Awareness: Engage People at Every Level
Human error remains one of the leading causes of data breaches. For this reason, awareness and training are integral to any ISMS. Employees should not only understand policies and procedures but also recognize how their actions affect overall security.
Regular awareness programs, phishing simulations, and targeted workshops help build a security-first culture, where staff act as active defenders rather than weak links.
6. Review and Continuous Improvement: Keep the ISMS Alive
Information security is a moving target. Threats evolve, technologies change, and businesses grow. A successful ISMS must therefore follow the Plan-Do-Check-Act (PDCA) cycle — a model for continuous improvement.
Periodic reviews, internal audits, and management evaluations ensure that controls remain effective and aligned with organizational priorities. Feedback loops make it possible to refine the system, strengthen weak points, and adapt to new challenges.
By following these six steps, organizations can move from isolated security initiatives to a mature, repeatable, and measurable framework — one that supports long-term resilience and regulatory compliance while building trust with stakeholders.
The Essential Components of a Robust ISMS
A strong Information Security Management System (ISMS) is built on more than policies and technical controls — it’s the result of an organization-wide ecosystem where governance, culture, and technology reinforce one another. Robustness comes from balance: strategic leadership, continuous evaluation, engaged people, and reliable tools, all working together to make information security a core business function.
Committed Leadership
At the heart of every effective ISMS lies committed leadership. Senior management must not only approve the security policy but actively champion it, demonstrating that information security is essential to the organization’s mission and resilience. When leaders allocate resources, communicate priorities, and hold themselves accountable, they signal to every employee that security is everyone’s responsibility.
This top-down commitment transforms the ISMS from a compliance framework into a strategic management tool, aligning risk management with business growth and trust-building.
Regular Evaluation and Monitoring
Yet leadership alone is not enough. A robust ISMS depends on a cycle of continuous evaluation to remain effective over time. Regular audits, performance reviews, and risk reassessments ensure that implemented controls keep pace with evolving threats and business objectives.
By using clear metrics and KPIs, organizations can detect weaknesses early and adapt quickly. This proactive approach turns compliance reporting into a genuine performance measurement exercise, one that drives ongoing improvement rather than administrative burden.
A Strong Security Culture
Technology and processes can only go so far without the engagement of people. An ISMS thrives within a strong security culture, where awareness and accountability extend beyond the IT department. Employees who understand how their actions affect the organization’s security posture are far more likely to report incidents, question suspicious behavior, and follow best practices.
Training, internal communications, and recognition programs help nurture this mindset. Over time, security becomes second nature — not an obligation, but a shared value that protects both the company and its clients.
Interdepartmental Collaboration
To make that culture effective, collaboration between departments is essential. Information security cannot function in silos. IT teams rely on HR to manage user access, procurement teams to assess vendor risks, and compliance officers to interpret regulations. A mature ISMS encourages regular dialogue among these groups, ensuring that decisions around risk, technology, and policy are consistent and transparent.
This cross-functional approach allows organizations to anticipate vulnerabilities before they escalate and respond faster when incidents occur.
Incident Response and Business Continuity
Even the best-prepared organizations face unexpected events, from data leaks to operational disruptions. A well-designed incident response and business continuity plan ensures that the ISMS doesn’t stop at prevention; it also enables swift, coordinated reaction. Clear roles, predefined communication channels, and recovery procedures minimize damage and downtime.
Beyond managing crises, these plans provide learning opportunities. Each incident becomes a source of insight that feeds into the ISMS’s continuous improvement loop, strengthening resilience with every iteration.
Technologies and Tools
Finally, no modern ISMS can function without the right technological backbone. Tools such as SIEM (Security Information and Event Management) systems, data loss prevention (DLP) solutions, and identity governance platforms help automate monitoring, detect anomalies, and support compliance reporting.
However, technology must serve strategy, not the other way around. A robust ISMS ensures that every tool is integrated into a coherent framework, supporting business goals while maintaining agility and scalability.
When these elements come together - leadership, evaluation, culture, collaboration, preparedness, and technology - the ISMS becomes more than a compliance mechanism. It evolves into a living system that adapts, learns, and continuously strengthens the organization’s capacity to protect what matters most: its information assets and reputation.

Ready to Strengthen Your Information Security?
Building and maintaining an effective Information Security Management System (ISMS) requires expertise, structure, and long-term vision. Our team of specialists can help you design, implement, and optimize your ISMS to align with ISO/IEC 27001 standards and your organization’s strategic goals.
The Benefits of an Effective ISMS
Implementing a well-designed Information Security Management System (ISMS) transforms information security from a reactive discipline into a strategic advantage. Beyond protecting data, it creates measurable business value, reinforcing trust, resilience, and operational efficiency across the organization.
When properly implemented and maintained, an ISMS delivers benefits that extend far beyond IT security.
Protection Against Internal and External Threats
The most immediate and visible benefit of an ISMS is improved protection against cyber threats. By identifying risks, defining controls, and maintaining ongoing monitoring, organizations build resilience against both internal and external attacks.
Instead of relying on fragmented or ad hoc defenses, an ISMS provides a structured, proactive framework, one that minimizes the likelihood of incidents and reduces their impact when they occur. This approach is especially valuable in today’s environment, where attacks are increasingly sophisticated and the margin for error is minimal.
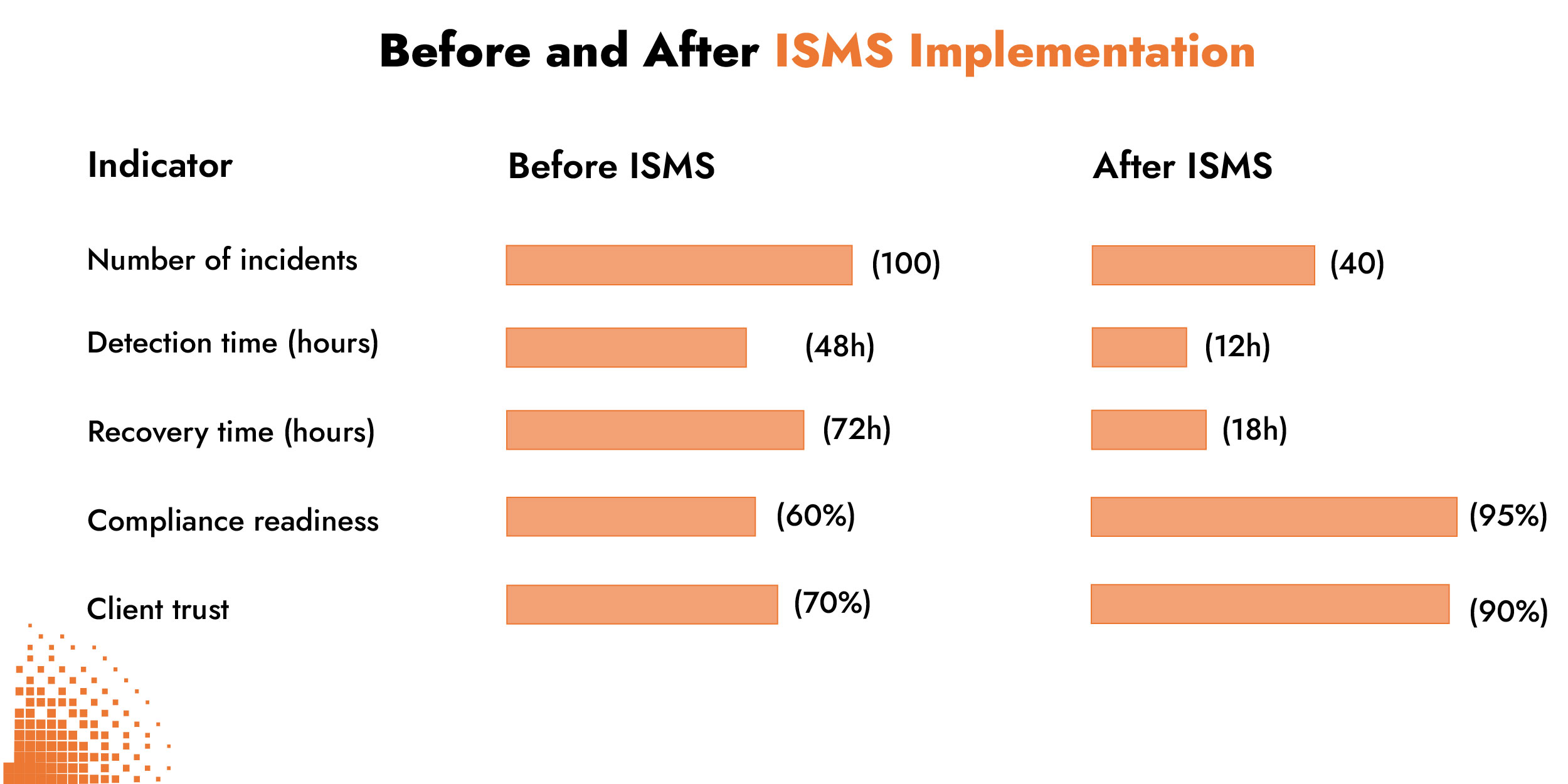
Strengthened Reputation and Stakeholder Confidence
Trust is a critical business asset. Customers, partners, and investors expect organizations to handle information responsibly and transparently. An effective ISMS, particularly one certified under ISO/IEC 27001, demonstrates that commitment.
Certification acts as a visible sign of reliability, reassuring clients that their data is protected according to international best practices. Internally, it also strengthens the organization’s brand by positioning security as a marker of professionalism and integrity.
Regulatory Compliance and Legal Assurance
In a regulatory landscape shaped by frameworks such as the General Data Protection Regulation (GDPR) and other data protection laws, compliance is not optional. An ISMS provides the governance structure and documentation necessary to meet these obligations systematically.
This reduces the risk of non-compliance penalties and simplifies audits, as the organization can demonstrate clear accountability for information security decisions. More importantly, it fosters a mindset of responsible data management, where compliance becomes the natural outcome of good governance rather than an administrative burden.
Operational Efficiency and Continuous Improvement
While the ISMS’s primary focus is security, its process-oriented design, particularly the Plan-Do-Check-Act (PDCA)cycle, drives operational excellence as well. By identifying redundancies, optimizing workflows, and clarifying responsibilities, organizations often find that efficiency improves alongside security.
The emphasis on continuous improvement ensures that the ISMS evolves in step with the business. New risks, technologies, and opportunities are integrated systematically, maintaining both relevance and effectiveness over time.
Assurance for Partners and Clients
Finally, a mature ISMS enhances business confidence across the value chain. Partners are more likely to collaborate with an organization that can demonstrate control over its information assets. Clients, in turn, view this assurance as a differentiator, a sign that their data will remain safe and that the company’s operations are resilient even under pressure.
This assurance builds long-term relationships founded on transparency, reliability, and shared standards of trust.
By integrating these benefits, an ISMS becomes much more than a compliance requirement - it evolves into a strategic governance model that safeguards reputation, sustains business continuity, and strengthens competitive advantage.
In a world where information is currency, an effective ISMS ensures that organizations not only protect their assets but also earn the trust that fuels growth and innovation.
Conclusion
Building an effective Information Security Management System (ISMS) is not simply about compliance — it’s about creating a culture of resilience and trust. By combining governance, technology, and human awareness, an ISMS transforms security from a technical constraint into a strategic pillar of performance.
Organizations that commit to this approach not only strengthen their defenses but also demonstrate transparency and accountability to clients, regulators, and partners.
Whether you’re just beginning your ISMS journey or seeking to enhance an existing framework, the key is consistency: evaluate, adapt, and improve continuously. In doing so, you ensure that security becomes an enabler of growth — not an obstacle to it.
If you’re looking to take the next step toward a more resilient security posture, our experts can help you design, implement, and optimize your ISMS in alignment with your business goals.
FAQ
What does an ISMS include?
An Information Security Management System includes the policies, procedures, processes, and controls an organization uses to manage information security risks. It covers governance, technology, training, and continuous improvement — all aligned with international standards such as ISO/IEC 27001.
Why is ISO/IEC 27001 important for ISMS implementation?
ISO/IEC 27001 provides a globally recognized framework for establishing and maintaining an ISMS. It ensures that security measures are risk-based, consistent, and auditable, helping organizations demonstrate compliance and build trust with clients and regulators.
How long does it take to implement an ISMS?
Implementation time depends on the organization’s size, complexity, and current maturity level. For most companies, the process takes between six months and one year — from initial risk assessment and policy design to deployment and internal audit — before certification readiness.

We build scalable solutions to quantify cyber risk in financial terms so organizations can make informed decisions to improve governance and resilience.






